Tuesday, November 25, 2008
Tuesday, September 23, 2008
Assignment No.1
A token ring is very effective under high sustained load, as no collisionscan occur and each slot may be used to carry a message, providing highthroughput. A token ring is less effective when the load is light (tokenprocessing takes longer than bus access, so any one packet can take longerto reach its destination), or sporadic.
http://www.arl.wustl.edu/~fredk/Courses/cs422/sp00/Answers
2.) Although security issues were not mentioned in this chapter, every network owner must consider them. Knowing that open networks all data to pass to every node, describe the posssible security concerns of open network achitectures. include the implicatiions of passing logon procedures, user IDs, and passwords openly on the network.
Content located on the Network may be the property of another person.
All information, data, text, software, music, sound, images, sketches, diagrams, photographs, graphics, renderings, CAD files, video, messages or any other materials whatsoever (collectively, "Content"), however posted to, maintained on, or transmitted via the Network, is the sole responsibility and property of the person from which such Content originated (the “Author”). This means that the Author, and not the Network or AFH, is entirely responsible for all Content that he or she uploads, posts, or transmits via the Network. In the event any Content is deemed illegal under applicable law, we will cooperate fully with applicable authorities in removing such Content and identifying its Author.
This type of network architecture are openly vulnerable for the possible malicious intrusions like worms, viruses and other malicious programs. Malicious person entering a network to damaged the entire system can easily passed causing great unfavourable effect. Passing logon procedure can be now favourable to the someone whose will is to destruct, they can now easily alter and use open information for their own purpose that against to the rights of the people all over the network.
The development of highly sophisticated computer technology causes the network security experts to create a more secure and safety measures for the private information but as this open network be implemented the whole system must be publicly accessed and the information security are wholly responsibility of someone who is the owner.
3. )Remembering the discussion of deadlocks, if you were designing a networked system, how would you manage the treat of deadlocks in your network? Consider all of the following: prevention, detection, avoidance, and recovery.
Prevention -
The importance of computer networking to achieve resource sharing and data sharing is widely recognized. Local networking to achieve high performance and reliability is inevitable for the future. As cost of logic and memory decreases, the cost of communications resources become increasingly significant and these resources must be increasingly shared. This heightens the possibility of deadlocks due to this sharing.
- their must be a mutual exclusive access in the network.
- their must be a condition for holding non-sharable resources.
- any request for certain files inn the network must be allocated, but it cannot request another resources unless it releases the resource that it holds.
- before requesting resources, we first check wheter they arre available or not to prevent hold and wait state.
Avoidance-
4.)Assuming you had sufficient funds to upgrade only one component for a system with which you are familiar, explain which component you would choose to upgrade to improve overall performance, and why?
True network bridge devices like the WET54G do not require device driver software installation in order to function, simplifying installation. Instead, network settings for the WET54G can be made through a browser-based administrative interface.
Like USB adapters, wireless Ethernet bridges can draw their power from the main cable connected to the host device. Ethernet bridges require a specialized Power over Ethernet (PoE) converter to make this work, however, whereas this functionality is automatic with USB. Without a PoE add-on, wireless Ethernet bridges need a separate power cord.
Wirelss Ethernet bridges commonly feature LED lights. The WET54G, for example, displays lights for power, Ethernet and Wi-Fi status.
Thursday, January 31, 2008
DVD Recording procedure
Menu: Project - Burn DVD from disk
This is the last step in the DVD creation process.
With our DVD Project having been Compiled, there are a set of files that DVD-lab has prepared for you in the Output folder as set in the Compile process. At this point, the DVD Author has choices as to how to convert this set of files into a DVD master disc. You can either use the DVD-lab built-in recording module or you can choose to use a third party DVD recording software such as Nero, Prassi, Gear, etc...
It is common that you are supplied with a DVD recording software that was bundled with your DVD-R/DVD+R burner. This software may be better optimized for your particular drive. The DVD-lab built-in DVD recording module is a general ASPI writing application and should work fine. In an ideal world, either one would work equally well.
DVD-lab Disc record window
The DVD-lab Disc record window is automatically detached. That means it runs as a separate process independent from DVD-lab, you could even close DVD-lab and the recording will continue.
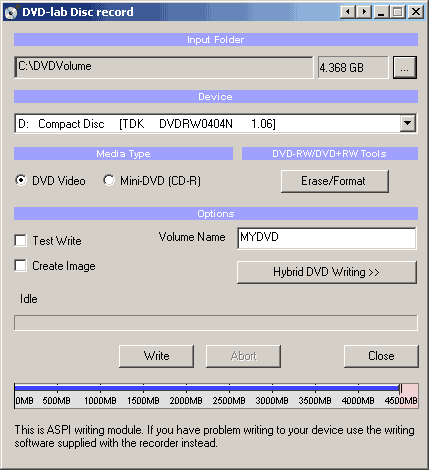
Here are some of the parameter choices for the DVD-lab Disc record window.
Input Folder
The Input Folder is the same as the Output folder in Compile. That means this is the folder where the VIDEO_TS and AUDIO_TS folders are expected to be.
Device
The DVD recording drive you want to write to, presented as the O/S recognizes it.
Media Type
Set if you want to burn DVD Video or a Mini-DVD.Mini-DVD is a DVD format burned on the CD-R. Obviously you can put far less data on a CD-R (about 700 MB) than on DVD (4.3 GB)
![]() The size indicator on the bottom can help you to determine how much data you can record to the disc. You have to keep your data below the red area.
The size indicator on the bottom can help you to determine how much data you can record to the disc. You have to keep your data below the red area.
![]() Note: While you will be able to play the CD-R on a computer not all standalone players will be able to play the Mini-DVD. In fact such format is not officially supported. The reason is that CD's have far less density of data so in order to play the large DVD video bitrate they have to spin much faster than DVD. Not all DVD drives in players are ready for this so the functionality to DVD files from CD-R is often simply disabled. However a number of Asian or re-branded Asian US models of players use a standard PC type of DVD drive which allows for fast spin of CD.
Note: While you will be able to play the CD-R on a computer not all standalone players will be able to play the Mini-DVD. In fact such format is not officially supported. The reason is that CD's have far less density of data so in order to play the large DVD video bitrate they have to spin much faster than DVD. Not all DVD drives in players are ready for this so the functionality to DVD files from CD-R is often simply disabled. However a number of Asian or re-branded Asian US models of players use a standard PC type of DVD drive which allows for fast spin of CD.
DVD-RW/DVD+RW Tools
For those using a re-writable media, the DVD-RW needs to be formatted if they were already used - click the Erase/Format button to do this. The more common DVD-R media do not need any formatting.
The DVD-RW and +RW needs to be finalized after writing. This takes quite a large amount of time on RW media. Please be patient until this important process is completed.
Options
Test Write checkboxUse this option by checking the Test Write checkbox to have DVD-lab do a trial run at writing a DVD. This option does not write anything to disk or your hard drive, it merely goes through the motions to insure that all of the content and menus within the DVD project are correctly prepared and defined.
Volume Name inputEnter here a name for the DVD volume that will appear when placed in a computer drive. A standalone DVD player just ignores this.
Create Image checkboxYou can choose to have DVD-lab create a large file on your hard drive which is an the image of a DVD disc instead of burning. The result will be one big IMG file. That IMG file can be used with a number of third party DVD recording software to replicate a DVD disc from this image file, as many times as you like, whenever you like. Some software will look for a ISO file name extension, if so, just rename the file to a .ISO extension. This method has the advantage of speed as the DVD image is all prepared on your hard drive, it is then a just matter of how fast your DVD burner drive will burn that image.
Hybrid DVD Writing buttonYou can add additional files and folders to the DVD master disc with the Hybrid DVD Writing option. What this option will do is setup an alternate filesystem on the DVD master disc which is called an ISO filesystem. The ISO format is what a standard CD uses while the DVD video is in UDF/ISO. This is perfectly DVD "legal" as the DVD player doesn't know or care about this ISO filesystem's contents, it just looks for a UDF filesystem.
It doesn't matter at all what the content or nature of these files are. They are just files, not Windows or Mac or Linux files, just files. As they are recorded into the ISO file system domain, they are available on any computer with a DVD drive. This offers the DVD-lab Author some creative options for bonus content that would be available to a computer user on any O/S that supports a DVD drive.

For example, you can create an autorun project in Multimedia Builder and record it to DVD as an extra feature when used on PC. HTML based content may be placed here as well, be sure to indicate to your computer users where to find your HTML starting page (ex: index.html).
Note: The space used by the Hybrid DVD Writing option counts in the entire Project space value. You only get so much space on a DVD (4.7G), this option uses part of that. Do the math to be sure you have room for this extra area.
Write buttonAs expected, click this button to start the DVD writing (burn) process.
Note: It is not recommended to do any work on the computer during DVD writing. Things like reading/writing to hard-drive may easily ruin your DVD-R. Try to let the burning process be the only thing your computer is running until it is completed.
Congratulations - now it is up to you to enjoy the DVD.
Wednesday, January 23, 2008
CPU type Package




FC-PGA Package TypeThe FC-PGA package is short for flip chip pin grid array, which have pins that are inserted into a socket. These chips are turned upside down so that the die or the part of the processor that makes up the computer chip is exposed on the top of the processor. By having the die exposed allows the thermal solution can be applied directly to the die, which allows for more efficient cooling of the chip. To enhance the performance of the package by decoupling the power and ground signals, FC-PGA processors have discrete capacitors and resistors on the bottom of the processor, in the capacitor placement area (center of processor). The pins on the bottom of the chip are staggered. In addition, the pins are arranged in a way that the processor can only be inserted one way into the socket. The FC-PGA package is used in Pentium® III and Intel® Celeron® processors, which use 370 pins.

OOI Package TypeOOI is short for OLGA. OLGA stands for Organic Land Grid Array. The OLGA chips also use a flip chip design, where the processor is attached to the substrate facedown for better signal integrity, more efficient heat removal and lower inductance. The OOI then has an Integrated Heat Spreader (IHS) that helps heatsink dissipation to a properly attached fan heatsink. The OOI is used by the Pentium 4 processor, which has 423 pins.


PPGA Package TypePPGA is short for Plastic Pin Grid Array, and these processors have pins that are inserted into a socket. To improve thermal conductivity, the PPGA uses a nickel plated copper heat slug on top of the processor. The pins on the bottom of the chip are staggered. In addition, the pins are arranged in a way that the processor can only be inserted one way into the socket. The PPGA package is used by early Intel Celeron processors, which have 370 pins.


S.E.C.C.2 Package TypeThe S.E.C.C.2 package is similar to the S.E.C.C. package except the S.E.C.C.2 uses less casing and does not include the thermal plate. The S.E.C.C.2 package was used in some later versions of the Pentium II processor and Pentium III processor (242 contacts).


S.E.P. Package TypeS.E.P. is short for Single Edge Processor. The S.E.P. package is similar to a S.E.C.C. or S.E.C.C.2 package but it has no covering. In addition, the substrate (circuit board) is visible from the bottom side. The S.E.P. package was used by early Intel Celeron processors, which have 242 contacts.
Tuesday, January 15, 2008
Types of form factor..
As mentioned earlier, motherboards are classified by form factors. Form factors essentially define the layout of the actual motherboard including the dimensions, component positioning, mounting holes, number of expansion slots, and so on. There are several different types of form factors including:
AT/Baby AT
ATX
LPX
BTX
NLX
The following sections will outline some of the characteristics of each of the form factors listed above, starting with the AT/Baby AT.
AT/Baby AT
The Advanced Technology (AT) was the original IBM form factor design, on which the processor, memory and expansion slots were all arranged in a straight line as shown in Figure A.
Figure A

AT was the original IBM form factor design.
This posed a problem for full length expansion cards because the height of the processor interfered with proper card installation. In addition, heat dissipation from the processor sometimes caused problems for the expansion cards. The AT form factor also caused problems with the drive bays. The width of the board was 12" wide and 13.8" deep which overlapped with the space required for drive bays.
The Baby AT was a smaller version of the AT, only 9" wide and 13" deep, with newer, smaller components. It was a more compact board, but had the same drawbacks as the AT. In a home PC this is rarely an issue. However, in servers, many expansion cards are full length. Traditionally servers are not designed around the Baby AT form factor.
As motherboards have evolved over the years, the AT/Baby AT form factors have become obsolete.
ATX
The ATX form factor was designed to overcome the problems associated with the AT/Baby AT form factors. As shown in Figure B, the ATX component layout is different from the AT. In the ATX form factor, the processor and memory are arranged at a right angle to the expansion slots, allowing room for the use of full-length expansion cards. In the newer computers, the combined height of the processor, heat sink, and cooling fan make it possible to insert full length cards in any other form factor, and most new computers (including servers) are built around the ATX form factor

The ATX form factor is different than that of the AT/Baby AT form factor
ATX motherboards also offer advanced power management features that make them ever more attractive to computer builders. For example, ATX motherboards offer a soft shutdown option, allowing the operating system to completely power down the computer without the user's having to press the power switch.
A full size ATX board is 12" wide and 9.6" deep. There is also a smaller version referred to as the Mini-ATX board, is 11.2" wide and 8.2" deep.
MicroATX
The MicroATX, introduced by Intel in 1997, is a compatible variation to the ATX board outlined above. As the name would imply, the MicroATX is smaller than the standard ATX board because of the reduced number of I/O slots on the board. Due to the fact that it is smaller than the standard ATX board, the MicroATX form factor reduces the cost of computers and is often used in lower-cost systems.
FlexATX
The FlexATX form factor was released by Intel as an addition to the MicroATX. This form factor, which is smaller than the MicroATX, is designed for lower-end, smaller, consumer orientated systems. Some FlexATX boards do not even include expansion slots which mean expansion is only possible through USB or firewire ports.
LPX
The LPX form factor is not a standard one but a non-standard proprietary one sometimes found in desktop computer models (as opposed to towers or mini towers). This form factor is characterized by an expansion board that runs parallel to the motherboard. A riser card arrangement is used for expansion cards thereby allowing for smaller cases. The disadvantage is that this limits the number of expansion cards available.
LPX motherboards are typically integrated and most have the video and sound components built-in. However, due in part to the fact that the form factor is non-standardized, the ATX form factor is more popular.
BTX
Balanced Technology Extended (BTX) form factor was released in 2003 by Intel. Unlike other form factors, this one did not evolve from an older form factor. Instead, it was a completely new form factor.
As shown in Figure C, the BTX form factor allows for more integrated onboard components because it is larger than ATX. The airflow path is optimized by moving the memory slots and expansion slots. This allows the main system board components to use the same airflow thereby requiring fewer fans and reducing noise.

Balanced Technology Extended (BTX) form factor was released in 2003 by Intel.
The three motherboards included in the BTX form factor are outlined below.
PicoBTX - This is the smallest BTX motherboard form factor. It uses four mounting holes and one expansion slot.
microBTX - This form factor is slightly smaller than the regular BTX but larger than the PicoBTX. It uses seven mounting holes and four expansion slots.
BTX - Also referred to as regularBTX, is the largest BTX form factor. It uses up to ten mounting holes and supports a maximum of seven expansion slots.
NLX
NLX has been a form factor in use with desktops for quite some time. It is a compact form factor, often referred to as a "low-profile application". NLX motherboards are easily distinguished by the riser card to which the expansion cards connect. The riser cards allow from two to four expansion cards to be plugged in. These expansion cards sit parallel to the motherboard.
Servers with this form factor offer power that is similar to the larger traditional servers, but in the size of a VCR. The obvious benefit of the NLX form factor is that the bulk of a traditional server is reduced to a space-saving smaller server. Additionally, servers assembled in a rack mount case can be secured to a rack, which can itself be secured to the floor, providing better equipment safety.
Table A summarizes the form factors outlined above, including what they are typically used for and the maximum number of slots.
Table A